WEBNET
LEAD
Opening Wireshark and added the picopico.key to the TLS decrypt tab
Preferences > Protocol > TLS > RSA keys list > Browse > picopico.key file > Apply
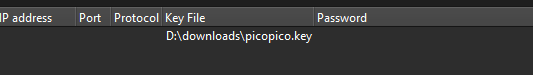
The information will change with the decrypted contents.
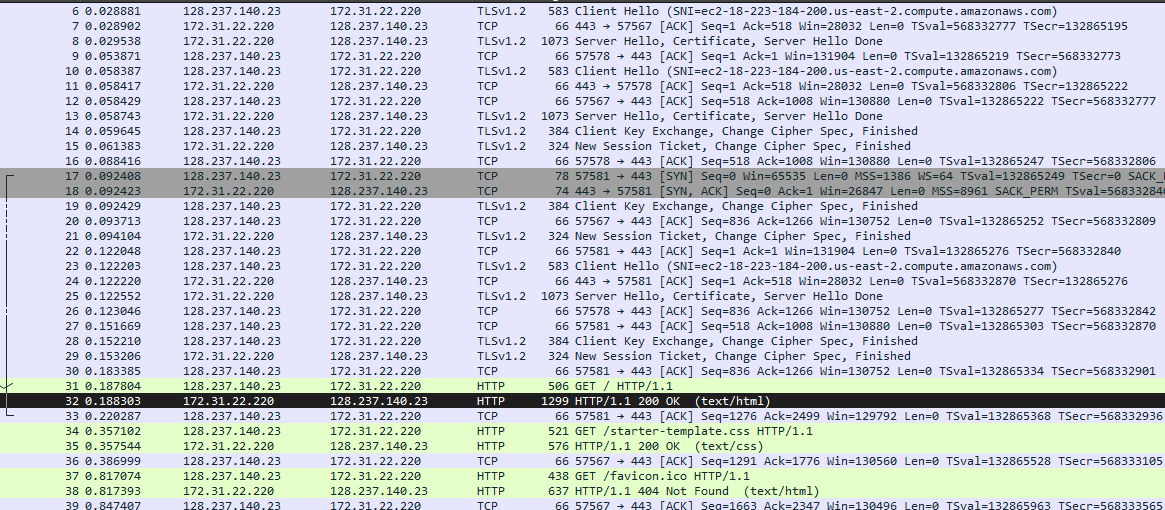
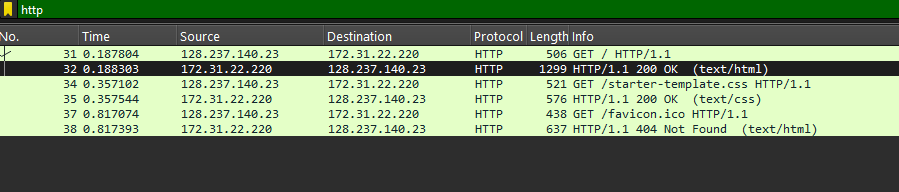
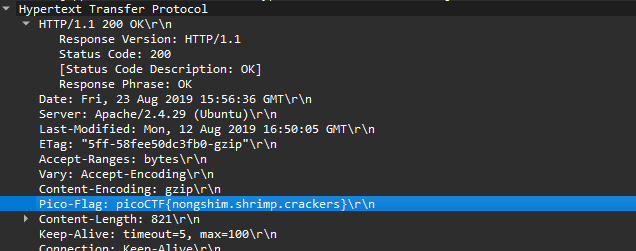
We then need to filter the HTTP sources and find the 200 OK Success HTTP request since we decrypted TLS it should appear in this HTTP’s packet contents