WHERE ARE THE ROBOTS
We will navigate to the robots.txt file , a commonly used file to prevent search engine web scrapers from paging and displaying it on search engines.
LEAD
Going to the Robots.txt , we can spot that there’s a disallowed directory
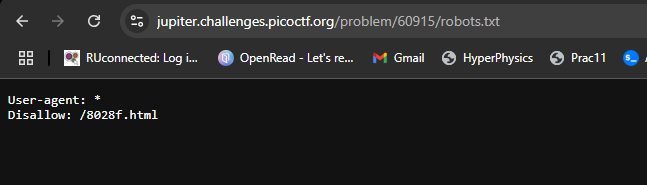
In the disallowed directory we have found the flag
FLAG
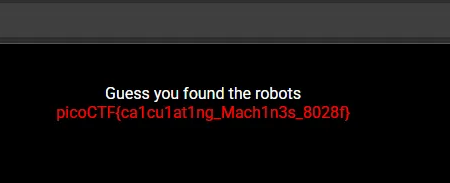
💡
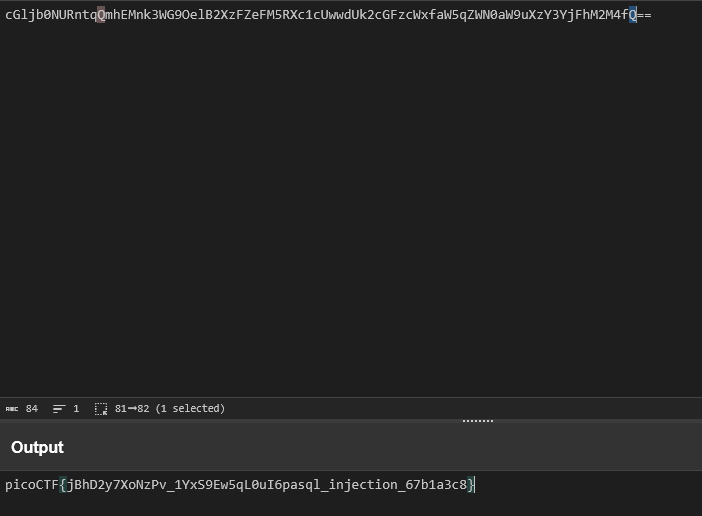
picoCTF{ca1cu1at1ng_Mach1n3s_8028f}
NoSql Injection
Download the files and look in the js file. This is where we can see the email and password that we need to find the flag
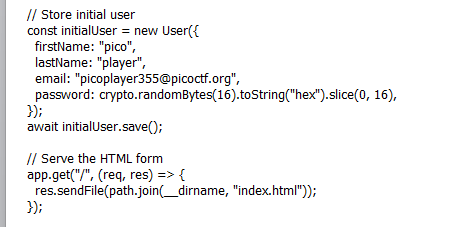
When entering the credentials given for the username and {”$ne”:”null”} in the password field.
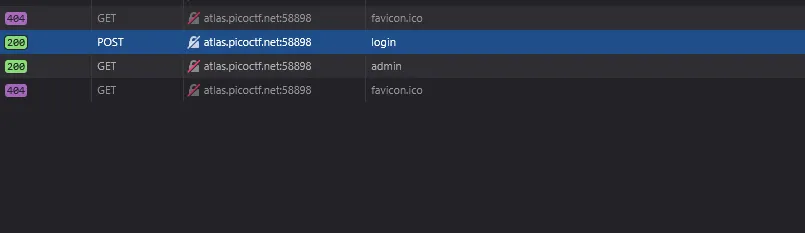
When monitoring the Network tab , we can see that a login POST request is sent with a token.
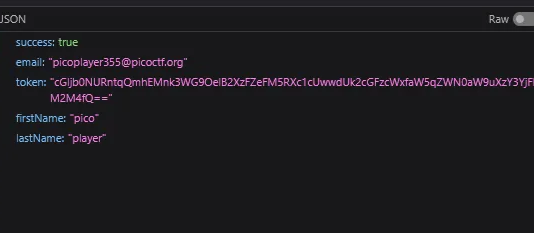
Converting the token using base64 we get the flag